The subject of data security is becoming a bigger issue for all users of the Internet. People may vary about their feelings regarding the level of personal responsibility they feel towards securing the data they present to the world, whether knowingly, or unknowingly, by engaging with the Internet, or VPNs.
It might be that your interface to the Internet is through a private company’s network, and that a lot of this concern is taken care of to do with company policy, but if you delve to the n’th degree, there are interfaces to the world not just where you work, but with communications such as email.
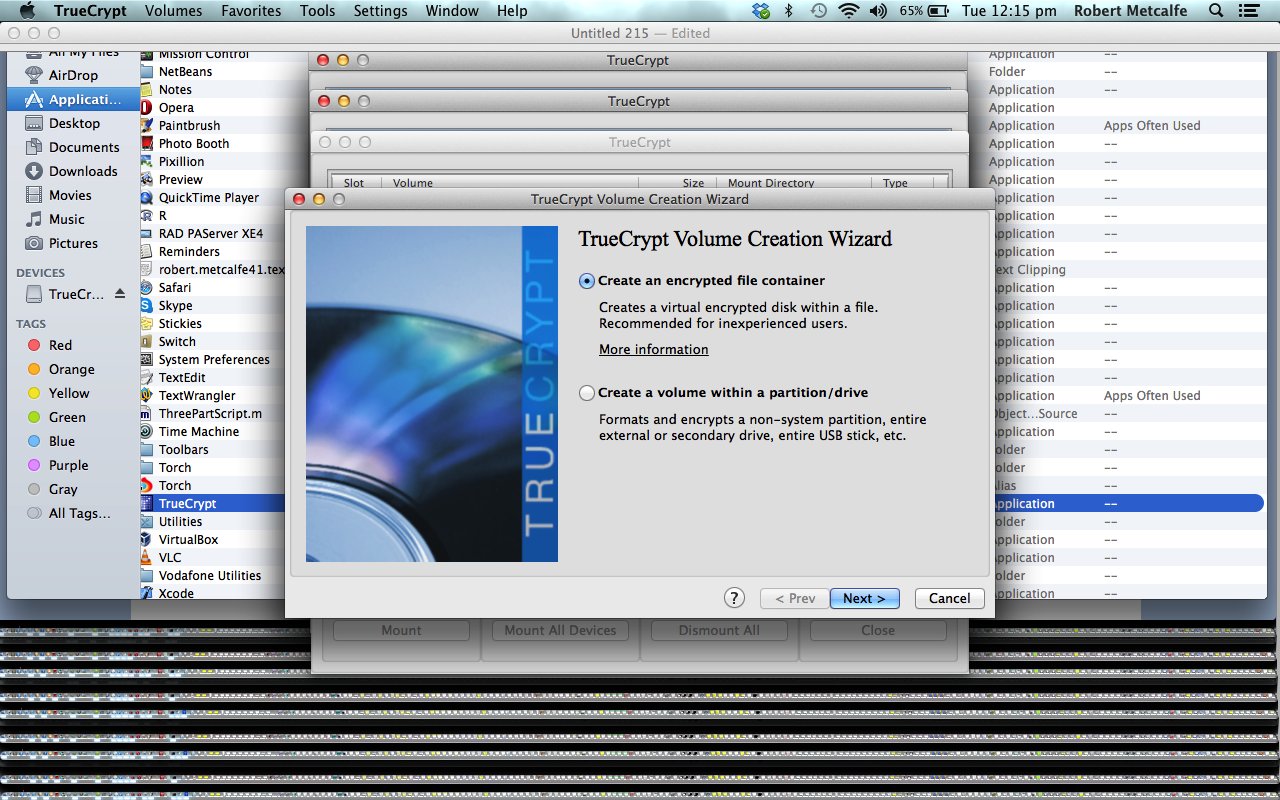
Today we show you some great data security software, called TrueCrypt, designed to be used to be able to encrypt the data files you wish to protect, whether that be via an encrypted individual file (container) or an encrypted volume or USB, for instance, or even “bigger” arrangements, for which expert advice may come into play … am not sure you should call Ghostbusters for this one?!
TrueCrypt is open source software designed for use with Windows or Mac (as for today’s tutorial install and “first try”), at the very least. Just installing it and setting up a small test shows that it can be manageable without that rocket science degree.
Whatever the case the use of data encryption is not a step to enter into, without looking into the issue a bit. As far as email goes, do some research into whether your email client perhaps encrypts for you … read here … but this is a huge topic area with some pretty high level expertise in the Information Technology industry. The other aspect you can be pretty sure about regarding this topic, is that it will be a topic of growing interest, rather than a shrinking petunia violet.
If this was interesting you may be interested in this too.